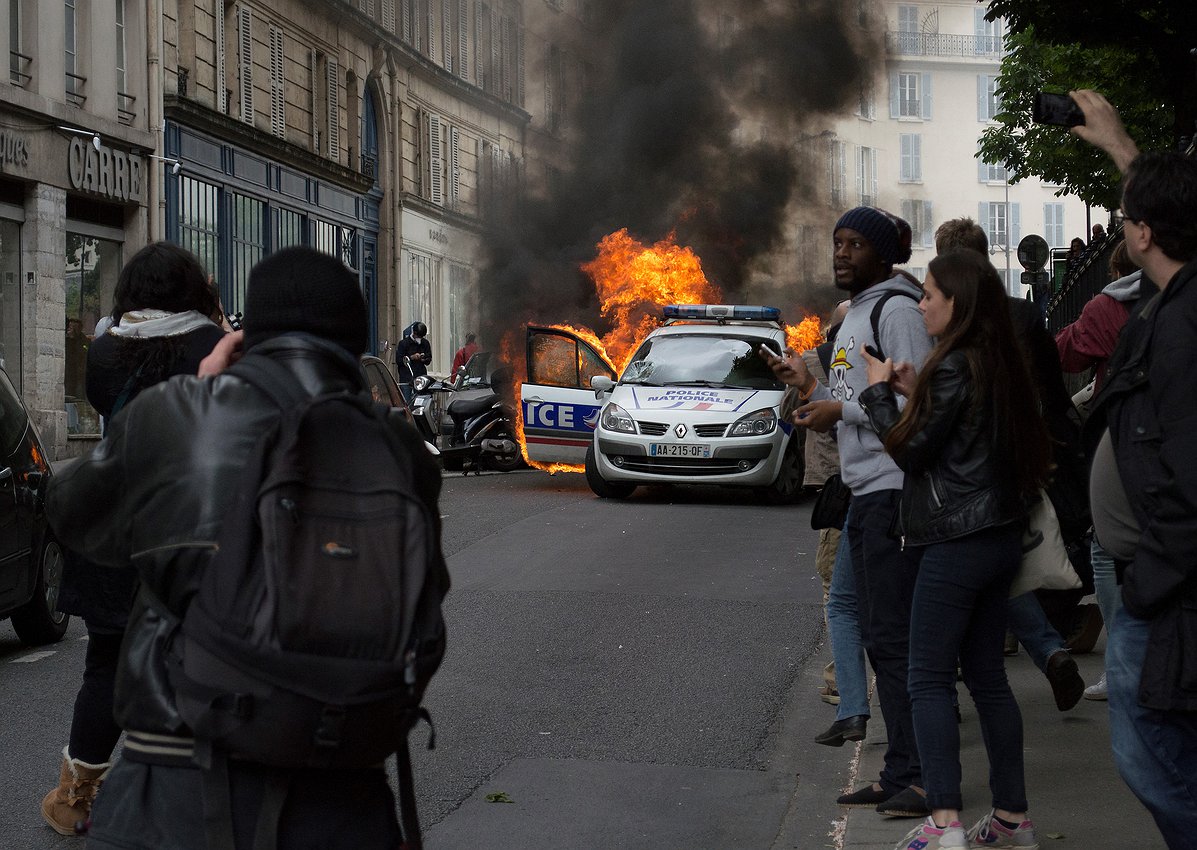For journalists covering political movements, reporting on protests is crucial, but these events come with unique security challenges. This guide, which was put together by Freedom of the Press Foundation, focuses on how U.S. journalists can manage the security of their devices and reporting materials when covering protests. Digital security is only one consideration, alongside both physical threats and your rights as a citizen and journalist.
Protecting your information
Before covering a protest, consider what data you’re bringing to the event, and what kinds of evidence you hope to take away. You also want to think about what would happen if any of that information left your custody. Depending on your situation, your devices might be lost, stolen, or confiscated by any number of groups — bystanders, demonstrators, authorities, and others. Ask yourself a few questions before attending the event:
- Do you have any sensitive data on your devices?
- How likely do you think it is that a third party could get access to your devices?
- Who could get access to your devices, and what might they be able to do?
- Do your web-connected devices have access to remote services, such as your email?
- Are there sensitive details that you need to obscure before publication, such as the identities of those involved? Would it be acceptable for them to be seen by someone before publication?
Sometimes protests can be relatively calm events. But sometimes protests can be chaotic. Press observers aren’t always distinguishable from the crowd; sometimes reporters even find themselves deliberately targeted by police, protesters or both. When protests become dynamic, equipment is generally more likely to be damaged, lost, stolen, or confiscated. Know the environment and the likely risks.
Need to protect your communications?
Before going anywhere, make sure your colleagues know where you are, and have your contact information.
Phone calls and SMS text messages can be easily intercepted. One common way SMS messages and phone calls are intercepted is using a fake cellphone tower, sometimes called an IMSI catcher or “Stingray.” Evidence compiled by Lucy Parsons Labs suggests IMSI catchers are being used by law enforcement officials around the globe. The good news is that it’s pretty easy to encrypt your mobile communications. Use Signal for iOS or Android to make secure phone calls and send secure text messages. If you want help getting started, read Signal for Beginners.
Keep in mind that your messages are only as secure as your phone. So if there’s no passcode, your phone can be opened with a simple swipe.
Keeping your data safe
You’ll want to make sure a record of what you saw at the event makes it out safely. Whatever form your media takes — physical film, or digital storage on a camera or smartphone — be prepared to physically secure your media.
Consider bringing a secondary mobile device
We all love to bring our mobile devices everywhere. But before bringing it to a protest, think carefully about what data is on your phone, and what might happen if it leaves your possession. Does it contain a great deal of sensitive or private information? Would losing access cause you significant problems? If so, consider bringing an alternative device instead.
Contract-free phones are fairly easy to find at corner stores and electronics shops and can typically be activated immediately after purchase. These devices are not nearly as secure as an up-to-date iPhone, for example, and encryption may not be on by default. On this secondary device, avoid logging into accounts with access to your personal data. If you plan on uploading video recordings on your mobile device, make sure to purchase a large data plan.
Remember that your colleagues may not know about your secondary phone; make sure you’ve exchanged numbers. You can put their numbers in your phone, but in case you lose access, write it down somewhere else as well.
If you need to bring your personal device, there are smart ways to do that.
Before covering an event, back up your mobile devices locally
If you’re going to bring your mobile device to the event, make a local backup of your data in case you lose access to your device. iPhones can make local backups. Learn how to back up files on your Android device.
Encrypt your devices
If your mobile device ever leaves your possession, the data on your hard disk can be read or copied. The good news is that it’s pretty easy to encrypt your disk. If you have a new password-protected iPhone, congratulations, your disk is already encrypted. Locking your phone is sufficient to encrypt the device — the longer the passcode, the better. For Android users, it’s pretty easy to encrypt your phone. Only a few Android phones are encrypted by default — the Google Pixel, Nexus 5X, 6P, 6, and 9. For Android devices, disk encryption is activated after powering down the phone entirely. It’s not enough to put the device into sleep mode.
(While you may not bring your laptop to an event, it’s still generally a good idea to encrypt your disk using your operating system’s native software, FileVault for Mac, or BitLocker on Windows. This is strongly advised for protecting your backups as well.)
Turn off mobile fingerprint lock
Fingerprints and passwords are treated quite differently by law enforcement. Right now, the legal protections for information inside of your mind — such as your password — are much stronger than information on your body. Turn off your fingerprint scanner when covering protests. You can turn it back on later.
iPhone users: Settings > Touch ID & Passcode
Android users (with Nexus devices): Settings > Security > Nexus Imprint
Live streaming comes with trade offs
Sometimes it’s easiest to take video with your mobile device. Live streaming a video online (e.g., via Facebook Live) can be extraordinarily useful for capturing an event. If your device is confiscated, but you live streamed the video, it’s already out in the world. But you’re also at the whim of the streaming service. For instance, Facebook can, and has cut off Live feeds at the request of law enforcement. You also risk sharing unblurred images of protest participants and bystanders. Consider the tradeoffs, and if streaming is a good choice for your situation.
Need to protect the people in your photos or videos?
It’s possible you don’t want to identify the individuals in your images or recordings. When you’re concerned about revealing the individuals in a video, use ObscuraCam for Android to blur faces in your footage. ObscuraCam is developed by a group called The Guardian Project; check out their other tools for digital security as well.
If you are going to upload videos to YouTube, WITNESS put together an excellent guide on using YouTube’s blurring tool to obscure the faces of those in your video.
Bonus: Use sensor data for verification.
Your phone is a beacon, transmitting an enormous amount of data about where you are, where you have been, and even where you might go. And while this can be a pain in other parts of our lives, when documenting an event this can be a valuable property for verifying the legitimacy of a photo or video. If this is a concern, use CameraV for Android (also developed by The Guardian Project) to attach rich sensor information to photos and videos.
Make sure you have enough power
Shooting video, live-tweeting, and calling your editor (hopefully via Signal!) all take a lot of juice. Be sure to bring a backup or external battery with sufficient power to recharge your phone at least two to three times. You’ll need it.
Physical concerns
Depending on the event you’re covering, physical injury can be a serious concern. Journalists are as vulnerable as anyone else at the event, and may even be targets because of their work. Even though this is illegal, it does happen. Buddy up if you can. And stay vigilant — both as to your own safety, as well as that of journalists around you.
In general, there isn’t a reliable way to encrypt photos and videos on a traditional camera, and this is a problem well recognized by photojournalists and filmmakers reporting from dangerous environments. Your primary defense for protecting physical films and storage devices is to keep them in your possession, and to make backups as soon as you can.
Know when to talk to a lawyer
The good news is the law is generally on your side. You have a First Amendment right to record public events. If authorities say you can’t record something happening in public at a demonstration, that’s almost certainly untrue. You also have a Fourth Amendment protection against unreasonable searches and seizures, meaning authorities are usually not permitted to search your smartphone without a warrant. (The rules are less clear regarding information stored in the cloud; on balance, it’s likely law enforcement will get a warrant for content stored offsite.) Similarly, law enforcement cannot delete your footage, photographs or posts, or force you to do so. In addition to implicating the First and Fourth Amendments, that would likely run afoul of the due process protections in the Fourteenth Amendment, as well.
In addition to the constitutional protections, there are state and federal statutes designed to safeguard the free flow of news. For example, with few exceptions, the federal Privacy Protection Act forbids law enforcement from searching and seizing journalists’ work product and documentary materials. This law applies to journalistic activity (e.g., freelancers and citizen journalists), not just journalists at traditional news organizations. With the exception of Wyoming, each state and the District of Columbia provide some protections that limit journalists’ obligation to testify about their stories or turn over unpublished materials in response to a subpoena. (The strength of these protections vary by state.) You can still get in trouble for breaking laws that apply to everybody. For example, journalists cannot trespass on private property, obstruct officers, or resist arrest, and law enforcement may use these and similarly neutral laws as a pretext to arrest you. Unfortunately, the threat of arrest is more than hypothetical — there are many examples of journalists being detained while covering events.
The Electronic Frontier Foundation’s advice here is sound:
If questioned by police, you can politely but firmly ask to speak to your attorney and politely but firmly request that all further questioning stop until your attorney is present. It is best to say nothing at all until you have a chance to talk to a lawyer. However, if you do decide to answer questions, be sure to tell the truth. It is likely a crime to lie to a police officer and you may find yourself in more trouble for lying to law enforcement than for whatever it was they wanted on your [device].
Of course, none of this general information about the law takes the place of actual legal advice from an attorney who knows the facts of your situation. If you are arrested or your devices are seized, heed the EFF’s advice and talk to a lawyer immediately. There are a number of terrific organizations that offer pro bono legal assistance:
- Your local affiliate of the American Civil Liberties Union.
- The Electronic Frontier Foundation.
- The Reporters Committee for Freedom of the Press legal defense hotline.
- The Student Press Law Center.
- The National Press Photographers Association
If you believe you are likely to run into trouble, consider writing your lawyer’s phone number on your arm before the event
Go get the story
For reporters covering protests, legal, physical, and digital safety are all very real concerns. There’s no replacement for knowing the environment and likely concerns in advance, then coming prepared. Learn more about common risks for protesters. They are putting themselves on the line to call attention to issues of political importance. Do them justice. Stay safe, and get the story.
The authors would like to thank Victoria Baranetsky of the Reporters Committee for Freedom of the Press and Riana Pfefferkorn of the Stanford Center for Internet and Society for their invaluable feedback on this post.
Except where otherwise noted, this work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International license by the authors.
Image by AFP.